A Visual Exploration of Exploits in the Wild
The Inaugural Study of EPSS Data and Performance
Our collaborative report, “A Visual Exploration of Exploitation in the Wild,” meticulously evaluates the Exploit Prediction Scoring System (EPSS) and its performance over recent years. Created by top cybersecurity experts, including Cyentia Emeritus Jay Jacobs, the EPSS creator and First.org EPSS SIG Co-chair, this report offers invaluable insights for defenders looking to prioritize vulnerability remediation efforts effectively.
Drawing from extensive data analysis, this report highlights the importance of feedback in improving cybersecurity practices. Just as athletes need feedback to enhance their performance, organizations must continually assess and refine their vulnerability management strategies. EPSS stands out by providing daily updated predictions based on real-world exploit data, enabling organizations to efficiently prioritize their remediation efforts.
This report compares EPSS with other prioritization strategies, such as the Common Vulnerability Scoring System (CVSS) and the Known Exploited Vulnerability (KEV) list, demonstrating EPSS’s superior ability to predict exploitation with higher accuracy and efficiency. This comprehensive evaluation is essential for security teams aiming to adopt the most effective vulnerability management strategies.
Preview The Inaugural Study of EPSS Data and Performance
What’s Inside the Report?
The report begins by addressing a common issue in the security industry: the lack of validation for security products and models. By providing a data-driven evaluation of EPSS predictions and their real-world impact, we aim to break this cycle. Over the years, data contributors have shared valuable exploitation activity, allowing us to train and refine the EPSS model. This rich history of predictions is now being tested with the benefit of hindsight, offering an unparalleled look into vulnerability exploitation.
Key Findings
The report addresses critical questions, including:
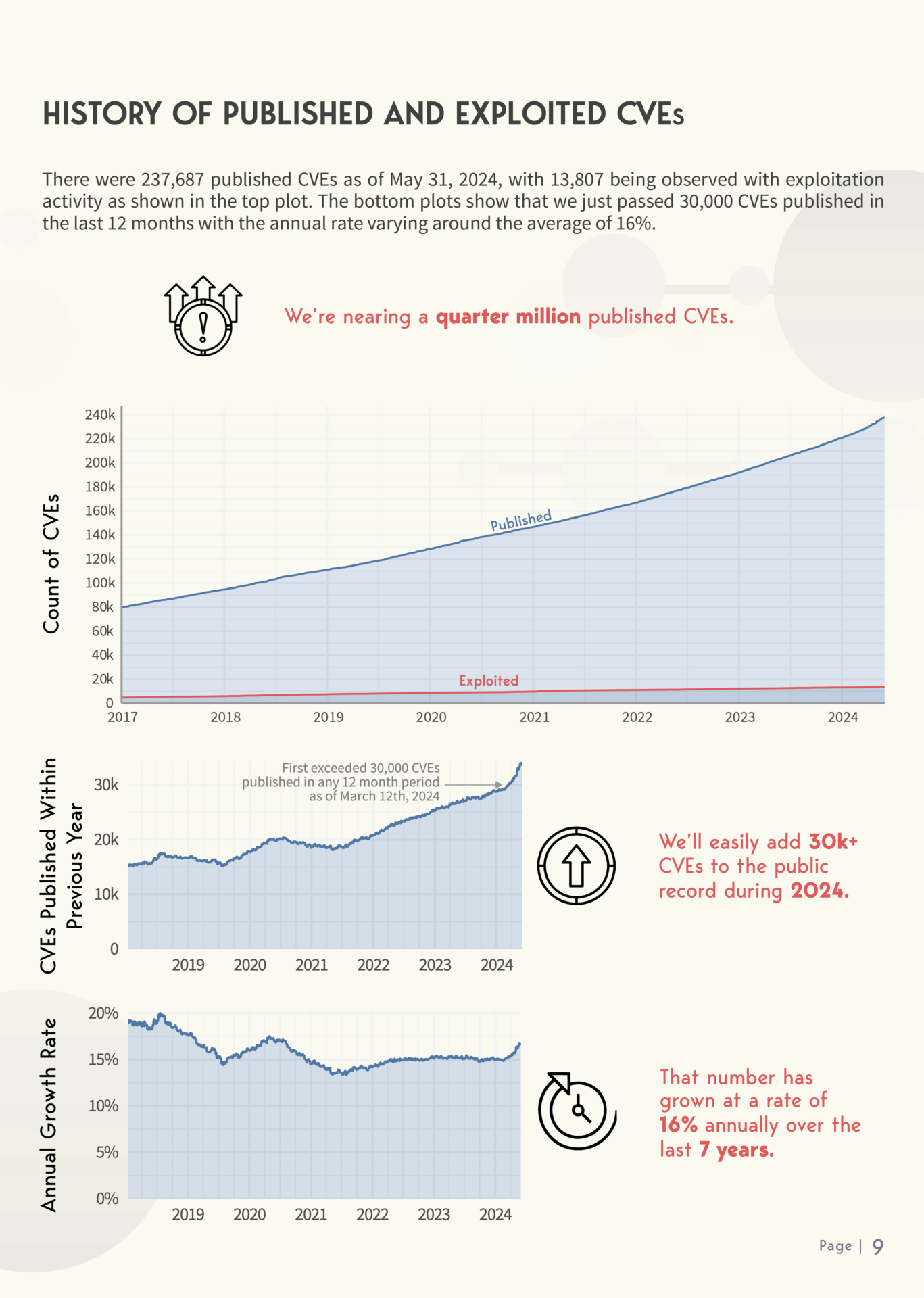
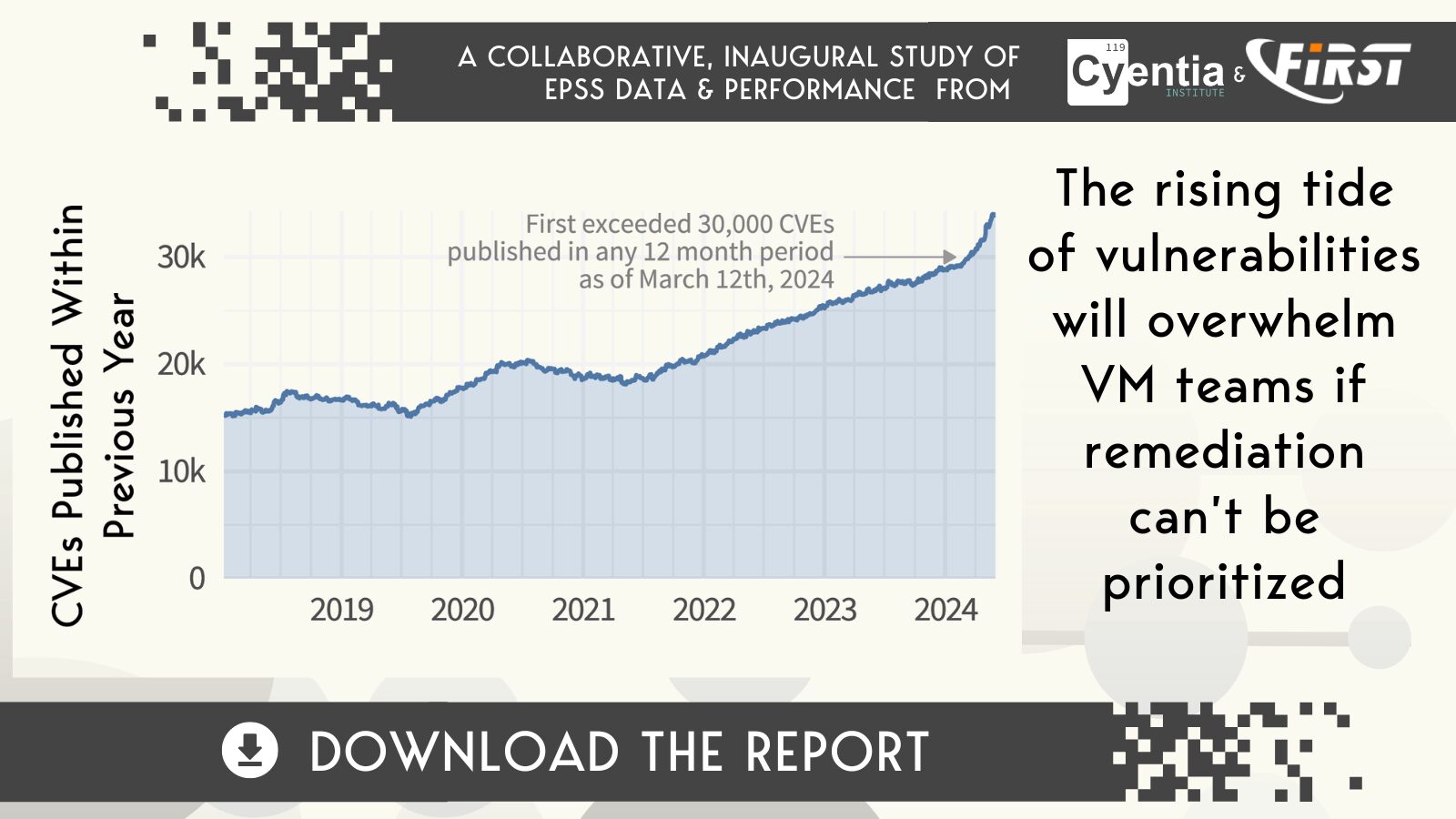
- How many vulnerabilities have been published and exploited?
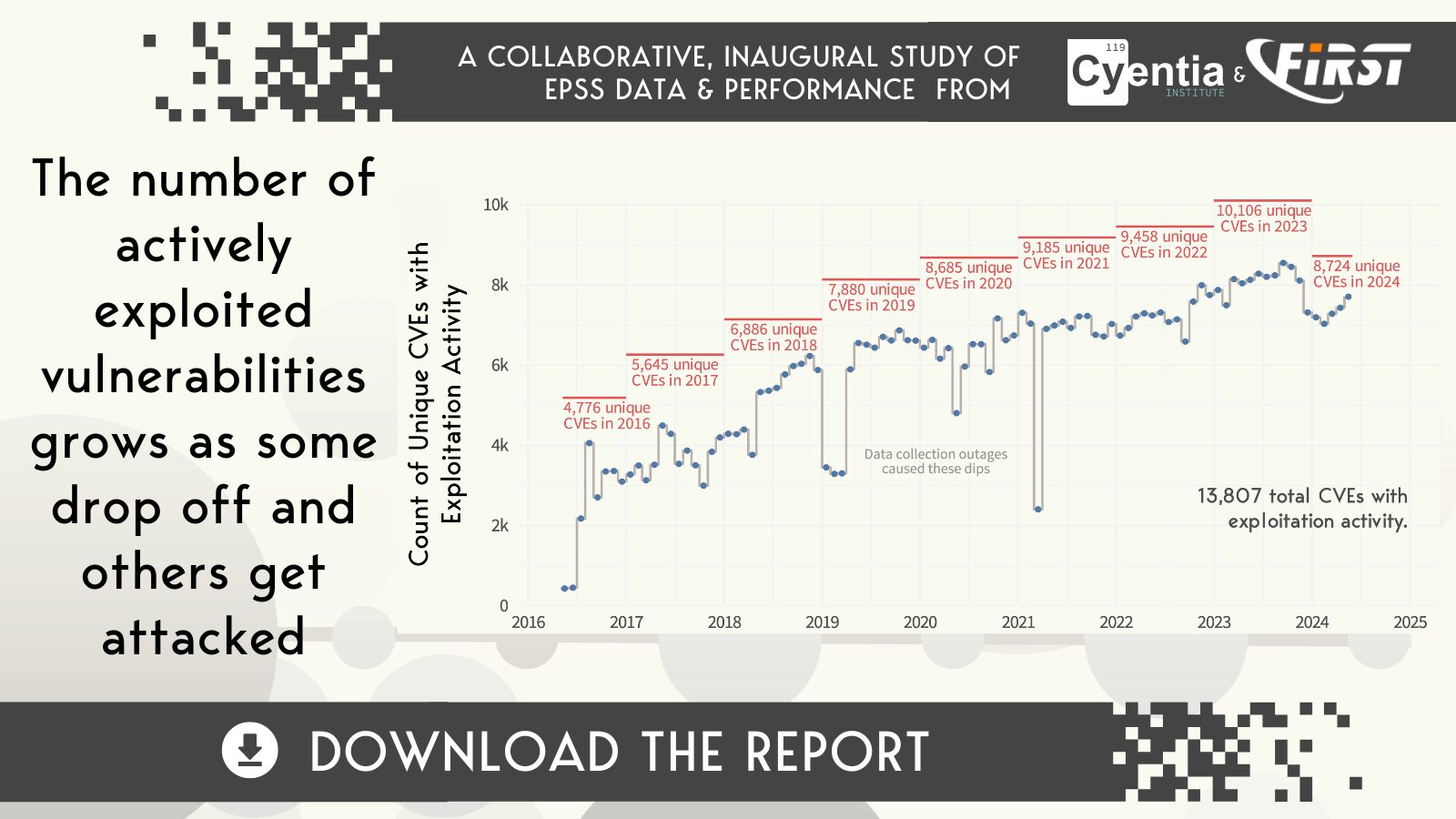
- Does exploitation activity fluctuate over time?
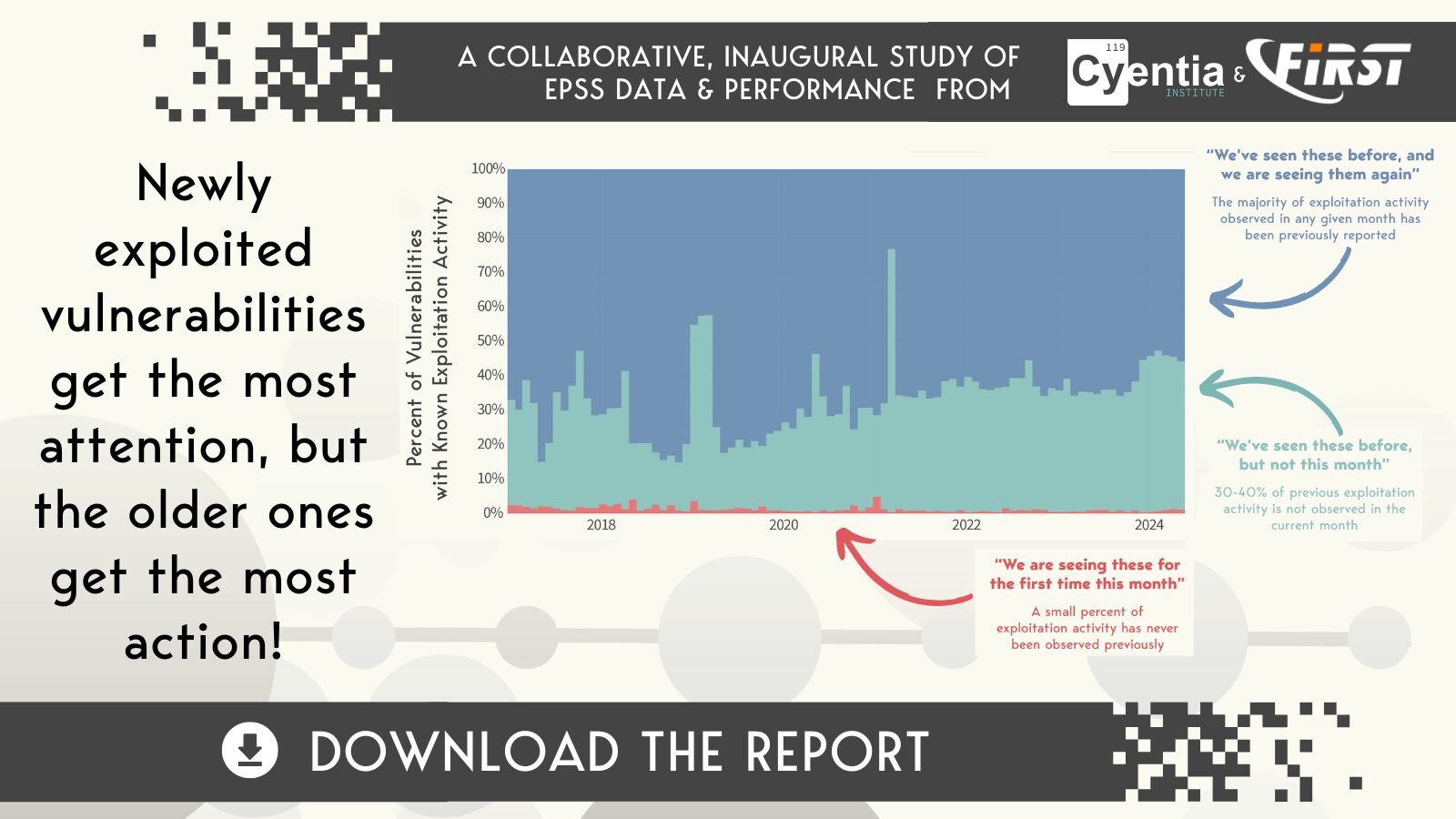
- What patterns of exploitation activity exist?
- How do EPSS predictions compare to systems like CVSS and the KEV list?
Through detailed analysis and visualization, the report reveals sporadic exploitation patterns and consistently targeted vulnerabilities, offering invaluable data for organizations to stay ahead of potential threats.